Kremlin-backed hackers have been exploiting a critical Microsoft vulnerability for four years in attacks that targeted a vast array of organizations with a previously undocumented tool, the software maker disclosed Monday.
When Microsoft patched the vulnerability in October 2022—at least two years after it came under attack by the Russian hackers—the company made no mention that it was under active exploitation. As of publication, the company’s advisory still made no mention of the in-the-wild targeting. Windows users frequently prioritize the installation of patches based on whether a vulnerability is likely to be exploited in real-world attacks.
Exploiting CVE-2022-38028, as the vulnerability is tracked, allows attackers to gain system privileges, the highest available in Windows, when combined with a separate exploit. Exploiting the flaw, which carries a 7.8 severity rating out of a possible 10, requires low existing privileges and little complexity. It resides in the Windows print spooler, a printer-management component that has harbored previous critical zero-days. Microsoft said at the time that it learned of the vulnerability from the US National Security Agency.
On Monday, Microsoft revealed that a hacking group tracked under the name Forest Blizzard has been exploiting CVE-2022-38028 since at least June 2020—and possibly as early as April 2019. The threat group—which is also tracked under names including APT28, Sednit, Sofacy, GRU Unit 26165, and Fancy Bear—has been linked by the US and the UK governments to Unit 26165 of the Main Intelligence Directorate, a Russian military intelligence arm better known as the GRU. Forest Blizzard focuses on intelligence gathering through the hacking of a wide array of organizations, mainly in the US, Europe, and the Middle East.
AdvertisementSince as early as April 2019, Forest Blizzard has been exploiting CVE-2022-38028 in attacks that, once system privileges are acquired, use a previously undocumented tool that Microsoft calls GooseEgg. The post-exploitation malware elevates privileges within a compromised system and goes on to provide a simple interface for installing additional pieces of malware that also run with system privileges. This additional malware, which includes credential stealers and tools for moving laterally through a compromised network, can be customized for each target.
“While a simple launcher application, GooseEgg is capable of spawning other applications specified at the command line with elevated permissions, allowing threat actors to support any follow-on objectives such as remote code execution, installing a backdoor, and moving laterally through compromised networks,” Microsoft officials wrote.
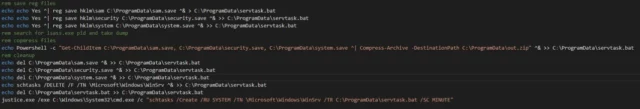
GooseEgg is typically installed using a simple batch script, which is executed following the successful exploitation of CVE-2022-38028 or another vulnerability, such as CVE-2023-23397, which Monday's advisory said has also been exploited by Forest Blizzard. The script is responsible for installing the GooseEgg binary, often named justice.exe or DefragmentSrv.exe, then ensuring that they run each time the infected machine is rebooted.
Microsoft representatives didn't respond to an email asking why the in-the-wild exploits are being reported only now.
Monday’s advisory provided additional technical details:
The GooseEgg binary—which has included but is not limited to the file names justice.exe and DefragmentSrv.exe—takes one of four commands, each with different run paths. While the binary appears to launch a trivial given command, in fact the binary does this in a unique and sophisticated manner, likely to help conceal the activity.
The first command issues a custom return code 0x6009F49F and exits, which could be indicative of a version number. The next two commands trigger the exploit and launch either a provided dynamic-link library (DLL) or executable with elevated permissions. The fourth and final command tests the exploit and checks that it has succeeded using the whoami command.
Microsoft has observed that the name of an embedded malicious DLL file typically includes the phrase “wayzgoose”; for example, wayzgoose23.dll. This DLL, as well as other components of the malware, are deployed to one of the following installation subdirectories, which is created under C:ProgramData. A subdirectory name is selected from the list below:
- Microsoft
- Adobe
- Comms
- Intel
- Kaspersky Lab
- Bitdefender
- ESET
- NVIDIA
- UbiSoft
- Steam
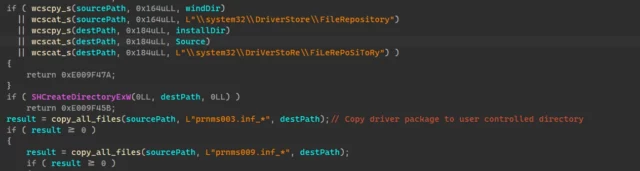
A specially crafted subdirectory with randomly generated numbers and the format string v%u.%02u.%04u is also created and serves as the install directory. For example, a directory that looks like C:ProgramDataAdobev2.116.4405 may be created. The binary then copies the following driver stores to this directory:
- C:WindowsSystem32DriverStoreFileRepositorypnms003.inf_*
- C:WindowsSystem32DriverStoreFileRepositorypnms009.inf_*
Enlarge / GooseEgg binary adding driver stores to an actor-controlled directory.Microsoft
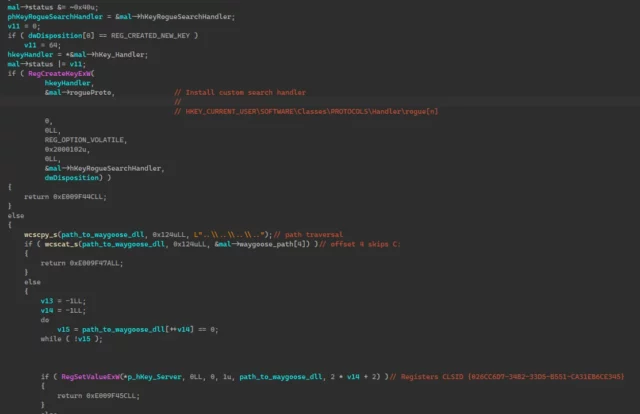
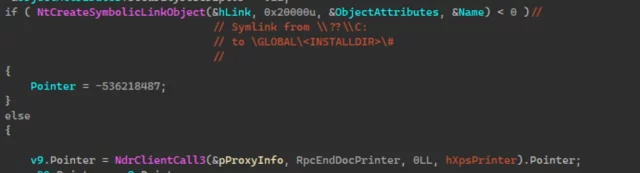
Next, registry keys are created, effectively generating a custom protocol handler and registering a new CLSID to serve as the COM server for this “rogue” protocol. The exploit replaces the C: drive symbolic link in the object manager to point to the newly created directory. When the PrintSpooler attempts to load C:WindowsSystem32DriverStoreFileRepositorypnms009.inf_amd64_a7412a554c9bc1fdMPDW-Constraints.js, it instead is redirected to the actor-controlled directory containing the copied driver packages.
Enlarge / GooseEgg registry key creationMicrosoft
Enlarge / GooseEgg C: drive symbolic link hijackMicrosoft
The “MPDW-constraints.js” stored within the actor-controlled directory has the following patch applied to the convertDevModeToPrintTicket function:
function convertDevModeToPrintTicket(devModeProperties, scriptContext, printTicket)
{try{ printTicket.XmlNode.load('rogue9471://go'); } catch (e) {}
The above patch to the convertDevModeToPrintTicket function invokes the “rogue” search protocol handler’s CLSID during the call to RpcEndDocPrinter. This results in the auxiliary DLL wayzgoose.dll launching in the context of the PrintSpooler service with SYSTEM permissions. wayzgoose.dll is a basic launcher application capable of spawning other applications specified at the command line with SYSTEM-level permissions, enabling threat actors to perform other malicious activities such as installing a backdoor, moving laterally through compromised networks, and remotely executing code.
People administering Windows machines should ensure that the fix for CVE-2022-38028 has been installed, as well as the fix for CVE-2021-34527, the tracking designation for a previous critical zero-day that came under mass attack in 2021. Monday’s advisory also provides more general advice on locking down the print spooler. Chief among the recommendations is to disable the service on domain controllers, the servers that act as the main gatekeeper inside Windows networks, where printing capabilities aren’t required.
AdvertisementPost updated to correct description of GooseEgg. It is a tool.