reader comments 16
reader comments 16 Hackers backed by a powerful nation-state have been exploiting two zero-day vulnerabilities in Cisco firewalls in a five-month-long campaign that breaks into government networks around the world, researchers reported Wednesday.
The attacks against Cisco’s Adaptive Security Appliances firewalls are the latest in a rash of network compromises that target firewalls, VPNs, and network-perimeter devices, which are designed to provide a moated gate of sorts that keeps remote hackers out. Over the past 18 months, threat actors—mainly backed by the Chinese government—have turned this security paradigm on its head in attacks that exploit previously unknown vulnerabilities in security appliances from the likes of Ivanti, Atlassian, Citrix, and Progress. These devices are ideal targets because they sit at the edge of a network, provide a direct pipeline to its most sensitive resources, and interact with virtually all incoming communications.
Cisco ASA likely one of several targets
On Wednesday, it was Cisco’s turn to warn that its ASA products have received such treatment. Since November, a previously unknown actor tracked as UAT4356 by Cisco and STORM-1849 by Microsoft has been exploiting two zero-days in attacks that go on to install two pieces of never-before-seen malware, researchers with Cisco’s Talos security team said. Notable traits in the attacks include:
- An advanced exploit chain that targeted multiple vulnerabilities, at least two of which were zero-days
- Two mature, full-feature backdoors that have never been seen before, one of which resided solely in memory to prevent detection
- Meticulous attention to hiding footprints by wiping any artifacts the backdoors may leave behind. In many cases, the wiping was customized based on characteristics of a specific target.
Those characteristics, combined with a small cast of selected targets all in government, have led Talos to assess that the attacks are the work of government-backed hackers motivated by espionage objectives.
“Our attribution assessment is based on the victimology, the significant level of tradecraft employed in terms of capability development and anti-forensic measures, and the identification and subsequent chaining together of 0-day vulnerabilities,” Talos researchers wrote. “For these reasons, we assess with high confidence that these actions were performed by a state-sponsored actor.”
The researchers also warned that the hacking campaign is likely targeting other devices besides the ASA. Notably, the researchers said they still don’t know how UAT4356 gained initial access, meaning the ASA vulnerabilities could be exploited only after one or more other currently unknown vulnerabilities—likely in network wares from Microsoft and others—were exploited.
“Regardless of your network equipment provider, now is the time to ensure that the devices are properly patched, logging to a central, secure location, and configured to have strong, multi-factor authentication (MFA),” the researchers wrote. Cisco has released security updates that patch the vulnerabilities and is urging all ASA users to install them promptly.
UAT4356 started work on the campaign no later than last July when it was developing and testing the exploits. By November, the threat group first set up the dedicated server infrastructure for the attacks, which began in earnest in January. The following image details the timeline:
One of the vulnerabilities, tracked as CVE-2024-20359, resides in a now-retired capability allowing for the preloading of VPN clients and plug-ins in ASA. It stems from improper validation of files when they’re read from the flash memory of a vulnerable device and allows for remote code execution with root system privileges when exploited. UAT4356 is exploiting it to backdoors Cisco tracks under the names Line Dancer and Line Runner. In at least one case, the threat actor is installing the backdoors by exploiting CVE-2024-20353, a separate ASA vulnerability with a severity rating of 8.6 out of a possible 10.
Line Dancer is a memory-only implant, meaning it has minimal reliance on any files stored on disk. Memory-resident malware is an advanced technique hackers use to allow their malware to escape many forms of detection. Once Line Dancer is installed, the hackers can use a simple unauthenticated web request to submit malicious code through the host-scan-reply field component.
“The host-scan-reply field, typically used in later parts of the SSL VPN session establishment process, is processed by ASA devices configured for SSL VPN, IPsec IKEv2 VPN with ‘client-services’ or HTTPS management access,” Talos researchers wrote. “The actor overrides the pointer to the default host-scan-reply code to instead point to the Line Dancer shellcode interpreter. This allows the actor to use POST requests to interact with the device without having to authenticate and interact directly through any traditional management interfaces.”
The researchers continued:
Line Dancer is used to execute commands on the compromised device. During our investigation, Talos was able to observe the threat actors using the Line Dancer malware implant to:
- Disable syslog.
- Run and exfiltrate the command show configuration.
- Create and exfiltrate packet captures.
- Execute CLI commands present in shellcode; this includes configuration mode commands and the ability to save them to memory (write mem).
- Hook the crash dump process, which forces the device to skip the crash dump generation and jump directly to a device reboot. This is designed to evade forensic analysis, as the crash dump would contain evidence of compromise and provide additional forensic details to investigators.
- Hook the AAA (Authentication, Authorization and Accounting) function to allow for a magic number authentication capability. When the attacker attempts to connect to the device using this magic number, they are able to establish a remote access VPN tunnel bypassing the configured AAA mechanisms. As an alternate form of access, a P12 blob is generated along with an associated certificate and exfiltrated to the actor along with a certificate-based tunnel configuration.
Host-Scan-Reply hook overview
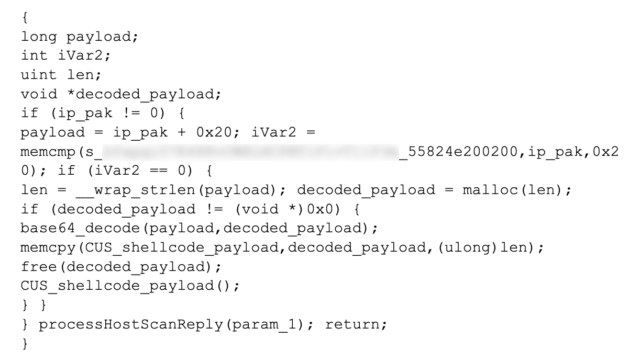
In the Line Dancer implant’s process memory, we found a function (detailed below) that checks if a 32-byte token matches a pattern. If so, it base64-decodes the payload, copies it into the attacker's writable and executable memory region, and then calls the newly decoded function. Either way, it ends by calling processHostScanReply().
The function processHostScanReply() is normally accessed through a function pointer in the elementArray table, associated with the string host-scan-reply. In the captured memory, the entry that should point to processHostScanReply() now instead points to the attacker's function that decodes and runs its payload. Since this change is in the data section of memory, it doesn't show up in hashes/dumps of text.
The attacker function that decodes and runs its payload has the following decompilation:
Line Runner, meanwhile, ensures that infections gain persistence, meaning they survive device reboots.
AdvertisementWednesday’s post provides extensive techniques and indicators that ASA users can employ to detect if they have been targeted or infected by the ongoing campaign. Recent campaigns targeting VPNs and firewall zero-days have often succeeded because they successfully exploited the vulnerabilities before admins installed patches. The takeaway should be that prioritizing the investigation of possible compromises and installation of security updates within the first 24 hours of an advisory is crucial.
Admins should also remember that the means of initial access by UAT4356 has yet to be determined, making it likely that patching the ASA vulnerabilities is likely only the beginning, and not the end, of the remediation process.