 reader comments 21
reader comments 21 Cybercriminals and spies working for nation-states are surreptitiously coexisting inside the same compromised name-brand routers as they use the devices to disguise attacks motivated both by financial gain and strategic espionage, researchers said.
In some cases, the coexistence is peaceful, as financially motivated hackers provide spies with access to already compromised routers in exchange for a fee, researchers from security firm Trend Micro reported Wednesday. In other cases, hackers working in nation-state-backed advanced persistent threat groups take control of devices previously hacked by the cybercrime groups. Sometimes the devices are independently compromised multiple times by different groups. The result is a free-for-all inside routers and, to a lesser extent, VPN devices and virtual private servers provided by hosting companies.
“Cybercriminals and Advanced Persistent Threat (APT) actors share a common interest in proxy anonymization layers and Virtual Private Network (VPN) nodes to hide traces of their presence and make detection of malicious activities more difficult,” Trend Micro researchers Feike Hacquebord and Fernando Merces wrote. “This shared interest results in malicious internet traffic blending financial and espionage motives.”
Pawn Storm, a spammer, and a proxy service
A good example is a network made up primarily of EdgeRouter devices sold by manufacturer Ubiquiti. After the FBI discovered it had been infected by a Kremlin-backed group and used as a botnet to camouflage ongoing attacks targeting governments, militaries, and other organizations worldwide, it commenced an operation in January to temporarily disinfect them.
The Russian hackers gained control after the devices were already infected with Moobot, which is botnet malware used by financially motivated threat actors not affiliated with the Russian government. These threat actors installed Moobot after first exploiting publicly known default administrator credentials that hadn’t been removed from the devices by the people who owned them. The Russian hackers—known by a variety of names including Pawn Storm, APT28, Forest Blizzard, Sofacy, and Sednit—then exploited a vulnerability in the Moobot malware and used it to install custom scripts and malware that turned the botnet into a global cyber espionage platform.
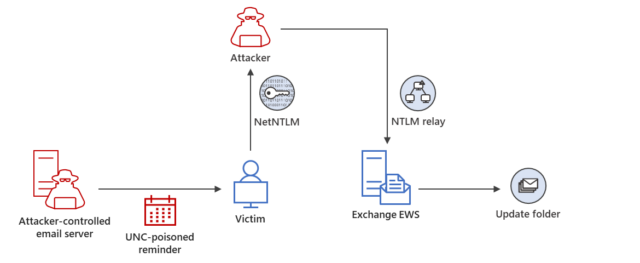
AdvertisementThe Trend Micro researchers said that Pawn Storm was using the hijacked botnet to proxy (1) logins that used stolen account credentials and (2) attacks that exploited a critical zero-day vulnerability in Microsoft Exchange that went unfixed until March 2023. The zero-day exploits allowed Pawn Storm to obtain the cryptographic hash of users’ Outlook passwords simply by sending them a specially formatted email. Once in possession of the hash, Pawn Storm performed a so-called NTLMv2 hash relay attack that funneled logins to the user accounts through one of the botnet devices. Microsoft provided a diagram of the attack pictured below:
Trend Micro observed the same botnet being used to send spam with pharmaceutical themes that have the hallmarks of what’s known as the Canadian Pharmacy gang. Yet another group installed malware known as Ngioweb on botnet devices. Ngioweb was first found in 2019 running on routers from DLink, Netgear, and other manufacturers, as well as other devices running Linux on top of x86, ARM, and MIPS hardware. The purpose of Ngioweb is to provide proxies individuals can use to route their online activities through a series of regularly changing IP addresses, particularly those located in the US with reputations for trustworthiness. It’s not clear precisely who uses the Ngioweb-powered service.
The Trend Micro researchers wrote:
In the specific case of the compromised Ubiquiti EdgeRouters, we observed that a botnet operator has been installing backdoored SSH servers and a suite of scripts on the compromised devices for years without much attention from the security industry, allowing persistent access. Another threat actor installed the Ngioweb malware that runs only in memory to add the bots to a commercially available residential proxy botnet. Pawn Storm most likely easily brute forced the credentials of the backdoored SSH servers and thus gained access to a pool of EdgeRouter devices they could abuse for various purposes.
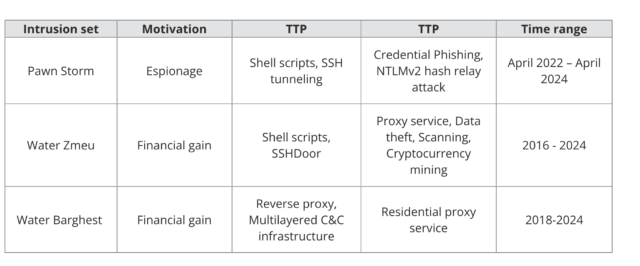
The researchers provided the following table, summarizing the botnet-sharing arrangement among Pawn Storm and the two other groups, tracked as Water Zmeu and Water Barghest:
It’s unclear if either of the groups was responsible for installing the previously mentioned Moobot malware that the FBI reported finding on the devices. If not, that would mean routers were independently infected by three financially motivated groups, in addition to Pawn Storm, further underscoring the ongoing rush by multiple threat groups to establish secret listening posts inside routers. Trend Micro researchers weren’t available to clarify. Advertisement
The post went on to report that while the January operation by the FBI put a dent in the infrastructure Pawn Storm depended on, legal constraints prevented the operation from preventing reinfection. What’s more, the botnet also comprised virtual public servers and Raspberry Pi devices that weren't affected by the FBI action.
“This means that despite the efforts of law enforcement, Pawn Storm still has access to many other compromised assets, including EdgeServers,” the Trend Micro report said. “For example, IP address 32[.]143[.]50[.]222 was used as an SMB reflector around February 8, 2024. The same IP address was used as a proxy in a credential phishing attack on February 6 2024 against various government officials around the world.”
Still going strong 8 years on
The botnet dates back to at least 2016 and has undergone multiple revisions over the years that have assembled a wide variety of hacking and proxy tools. The researchers wrote:
The malicious code consists of a collection of bash scripts, Python scripts, and a few malicious Linux binaries like SSHDoor. Functions in the bash scripts include the ability to retrieve specific information on the compromised hosts, including folders, system users, computing power, installed software, cryptocurrency wallets, passwords, and internet speed—valuable information to attacker groups. The collection of scripts also contains a script to install a SOCKS5 proxy with and without authentication, and a function to connect to the C&C server to upload information and download additional components. On compromised VPS hosts or routers with sufficient computing power, additional components for mining the Monero cryptocurrency might also be present.
A key element in the suite of scripts and malicious binaries is SSHDoor, a backdoored SSH daemon that allows attackers to steal legitimate credentials while users log in. It also makes persistent access possible, either through an SSH public key pair or via extra credentials that may be used by the malicious actor to log in. It is likely that the latter function was used by Pawn Storm to gain access to botnet’s nodes since its operator poorly protected their stolen assets. According to our research, the botnet operator used SSHDoor binaries that are available on public repositories while only minimally modifying the default credentials, making brute forcing the extra credentials in the backdoored SSH server an easy task for an adversary like Pawn Storm.
Though the FBI advisory mainly talks about Ubiquiti EdgeRouters being part of the botnet, Trend Micro’s telemetry and our research found that more Linux based devices are part of the botnet. In fact, any Linux-based internet facing router could be affected, especially those that were shipped with default credentials. In particular, Raspberry Pi devices and VPS servers in datacenters that form an XMRig mining pool for Monero cryptocurrency are part of the same botnet.
Enlarge / Statistics on Monero mining by a pool of VPS servers that are part of the botnet that was partially taken down by the FBI in January 2024. We have evidence that the botnet operator controls more Monero mining pools aside from this one.
Trend Micro
A large number of the bots also have an open SOCKS5 server, which we later identified to be MicroSocks, an open source SOCKS5 server software. Note that connections to these SOCKS5 servers may originate from anywhere. The port on which the SOCKS5 server is running is usually reported back to a C&C server of the botnet that the FBI disrupted. In some cases, the actor used a slightly different adapted version of MicroSocks with both the listening address (all interfaces) and port (56981/tcp) predefined.
The MicroSocks binary is commonly located at /root/.tmp/local. In late February 2024, the threat actors added authentication with a username and password in MicroSocks, recompiled it, and then reuploaded it to the bots.
The Trend Micro post was published on the same day that researchers from security firm Fortinet reported the discovery of a new botnet that targets a 9-year-old vulnerability in DLink routers.
AdvertisementThe Trend Micro and Fortinet reports follow a separate FBI operation in January that removed malware an espionage group backed by the Chinese government was using to proxy traffic through home and office routers from Cisco, Netgear, and others. The high quality of the C++ code and its “firmware agnostic” approach to establish covert communications channels on routers from virtually any manufacturer illustrate the importance these botnets have to the Chinese government.
Other advanced router malware seen in recent years includes VPN Filter and its successor Cyclops Blink—both attributed to the Russian government—HiatusRAT and ZuoRAT. With so many competing actors and malware packages targeting routers, it’s easy to see how they can coexist on the same devices.
The best way to keep routers free of this sort of malware is to ensure that their administrative access is protected by a strong password, meaning one that’s randomly generated and at least 11 characters long and ideally includes a mix of letters, numbers, or special characters. Remote access should be turned off unless the capability is truly needed and is configured by someone experienced. Firmware updates should be installed promptly. It’s also a good idea to regularly restart routers since most malware for the devices can’t survive a reboot. Once a device is no longer supported by the manufacturer, people who can afford to should replace it with a new one.