 reader comments 14
reader comments 14 Highly capable hackers are rooting multiple corporate networks by exploiting a maximum-severity zero-day vulnerability in a firewall product from Palo Alto Networks, researchers said Friday.
The vulnerability, which has been under active exploitation for at least two weeks now, allows the hackers with no authentication to execute malicious code with root privileges, the highest possible level of system access, researchers said. The extent of the compromise, along with the ease of exploitation, has earned the CVE-2024-3400 vulnerability the maximum severity rating of 10.0. The ongoing attacks are the latest in a rash of attacks aimed at firewalls, VPNs, and file-transfer appliances, which are popular targets because of their wealth of vulnerabilities and direct pipeline into the most sensitive parts of a network.
“Highly capable” UTA0218 likely to be joined by others
The zero-day is present in PAN-OS 10.2, PAN-OS 11.0, and/or PAN-OS 11.1 firewalls when they are configured to use both the GlobalProtect gateway and device telemetry. Palo Alto Networks has yet to patch the vulnerability but is urging affected customers to follow the workaround and mitigation guidance provided here. The advice includes enabling Threat ID 95187 for those with subscriptions to the company’s Threat Prevention service and ensuring vulnerability protection has been applied to their GlobalProtect interface. When that’s not possible, customers should temporarily disable telemetry until a patch is available.
Advertisement
Volexity, the security firm that discovered the zero-day attacks, said that it’s currently unable to tie the attackers to any previously known groups. However, based on the resources required and the organizations targeted, they are "highly capable" and likely backed by a nation-state. So far, only a single threat group—which Volexity tracks as UTA0218—is known to be leveraging the vulnerability in limited attacks. The company warned that as new groups learn of the vulnerability, CVE-2024-3400, is likely to come under mass exploitation, just as recent zero-days affecting products from the likes of Ivanti, Atlassian, Citrix, and Progress have in recent months.
“As with previous public disclosures of vulnerabilities in these kinds of devices, Volexity assesses that it is likely a spike in exploitation will be observed over the next few days by UTA0218 and potentially other threat actors who may develop exploits for this vulnerability,” company researchers wrote Friday. “This spike in activity will be driven by the urgency of this window of access closing due to mitigations and patches being deployed. It is therefore imperative that organizations act quickly to deploy recommended mitigations and perform compromise reviews of their devices to check whether further internal investigation of their networks is required.”
The earliest attacks Volexity has seen took place on March 26 in what company researchers suspect was UTA0218 testing the vulnerability by placing zero-byte files on firewall devices to validate exploitability. On April 7, the researchers observed the group trying unsuccessfully to install a backdoor on a customer’s firewall. Three days later, the group’s attacks were successfully deploying malicious payloads. Since then, the threat group has deployed custom, never-before-seen post-exploitation malware. The backdoor, which is written in the Python language, allows the attackers to use specially crafted network requests to execute additional commands on hacked devices.
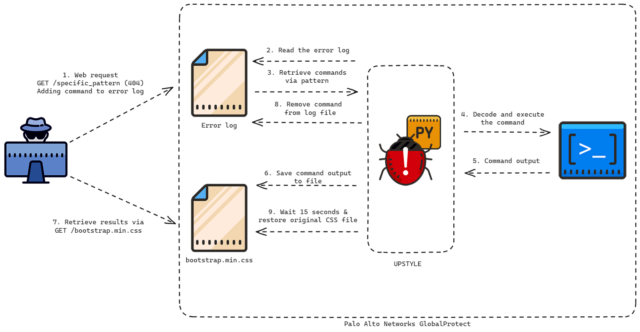
One of the files recovered by Volexity was named update.py, which UTA0218 unsuccessfully tried to download and execute using the CVE-2024-3400 zero-day. Company researchers provided the following analysis of the backdoor, which they track under the name Upstyle:
The purpose of the update.py script is to deploy a backdoor to the following path: /usr/lib/python3.6/site-packages/system.pth. The backdoor, written in Python, starts by an import and its main content is stored as a base64 encoded blob. The .pth extension is used to append additional paths to a Python module. Starting with the release of Python 3.5, lines in .pth files beginning with the text “import” followed by a space or a tab, are executed as described in the official documentation. Therefore, by creating this file, each time any other code on the device attempts to import the module, the malicious code is executed.
The commands to be executed are forged by the attacker by requesting a non-existent web page which contains the specific pattern. The backdoor’s purpose is to then parse the web server error log (/var/log/pan/sslvpn_ngx_error.log) looking for the pattern, and to parse and decode data added to the non-existent URI, executing the command contained within. The command output is then appended to a CSS file which is a legitimate part of the firewall (/var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css).
After the command’s execution is complete and the output has been written, the log entry that was originally read and contained the command is removed from the sslvpn_ngx_error.log file. Fifteen seconds after execution, the original version of bootstrap.min.css is also restored to its previous state. The access and modified timestamps are also restored for both files.
The following image illustrates how CVE-2024-3400 and Upstyle fit together:
Advertisement
Targeting keys to the kingdom
Once inside a network, UTA0218 is targeting and stealing some of the most sensitive resources available in a Microsoft network. Resources include the Active Directory databases for managing and allocating user accounrts, encryption keys for use with the Data Protection API, and Windows event logs storing secrets for use with the Remote Desktop Protocol. The attackers also stole login data, authentication cookies, and other sensitive data for both the Chrome and Edge browsers for use in obtaining the browser master keys and decrypting encrypted credentials stored inside.
UTA0218 uses a mix of infrastructure comprising servers hosting malware for use in communication channels and anonymized systems for accessing tooling and interacting with compromised networks.
“The anonymized infrastructure appears to have included a mix of VPN usage, as well as potentially compromised ASUS routers,” Volexity researchers wrote. “The infrastructure was used to access files created by the attacker. Additionally, UTA0218 abused a compromised AWS bucket and various Virtual Private Servers (VPS) providers to store malicious files.”
Any organization that uses a vulnerable configuration of a PAN firewall should make investigating and any necessary remediation a top priority. Volexity, security firm Rapid7, and Palo Alto Networks provide indicators of compromise and detection guidance here, here, and here.



















